Categories
Guest Highlight: Two Essential Elements of Cloud Security
January 2, 2025
Malcolm Harkins, Chief Security and Trust Officer at Cylance, on Proactive and Automated Cloud Security
In the post Two Essential Elements of Cloud Security, we talked about why your cloud security posture must be proactive and automated for you to get the best business value from the cloud, while protecting your business and avoiding ridiculous security complexity/costs.
We spoke with Malcolm Harkins, one of our advisors and the Chief Security and Trust Officer at Cylance, to get his perspective on why proactivity and automation are cloud security essentials. A notable security expert and author of Managing Risk and Information Security, Harkins is a leading advocate of the Protect To Enable security paradigm.
Q: Can you tell us more about the Protect to Enable security paradigm and why you think it’s important in today’s digital landscape?
In the Protect to Enable paradigm, the goal of a security posture is to enable business value by proactively protecting the business’s employees, customers, and data. When you are protecting to enable people, data, and the business, you are proactively engaged upfront and aligned with the business on the evaluation of how to achieve the business objective while best optimizing your security controls. As the digital economy grows, we have a responsibility to understand the dynamics of risk to our organizations, shareholders, customers, and society. That is the best way to prevent risk that is avoidable in a proactive fashion.
Q: How would you compare the Protect to Enable approach with the Detect and Respond approach?
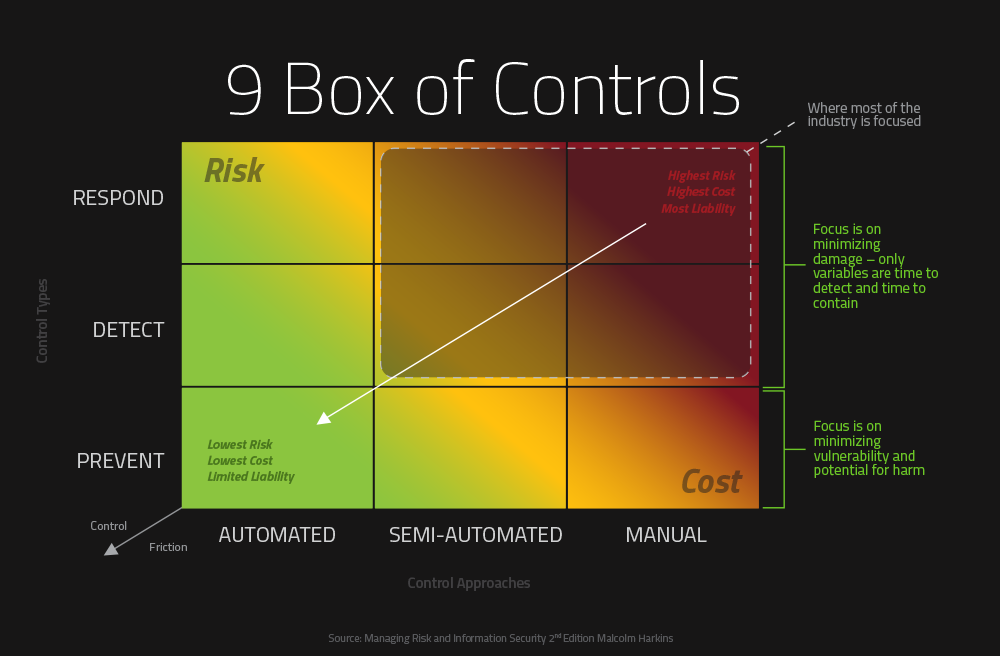
Detect and Respond (reactive) controls will always be needed because you cannot eliminate all risk – but you can prevent +99%. Companies that focus primarily on a reactive approach to handle risk expose themselves to ongoing higher risks and long-term higher costs since they are responding to attacks that have already gotten past their defenses. My 9 Box of Controls (below) shows that most organizations and security vendors focus on this approach, opting to allow such high risks and costs because they believe the industry narrative that attacks will succeed and that there isn’t a better approach. As I have said before, there’s profit to be made by many in the industry from not solving the root cause of the insecurity of computing.
Q: How is the Protect to Enable paradigm more effective in today’s digital landscape?
In my view, the magic quadrant for information security is not the upper right of my 9 Box of Controls, but the exact opposite – the lower left. As the digital landscape changes more rapidly, not only will attacks become more sophisticated and numerous (as recent headlines have shown), organizations will also be unable to scale their security postures if primarily using a reactive approach. In this situation, organizations impede their business through increased costs, loss of time and velocity, and damage to their resources and credibility. If we implement automated controls with a low degree of control friction that prevent risk all around, we are delivering exactly what the security industry so sorely needs – solutions that Protect to Enable people, data, and the business. In other words, automation allows security postures to be effective at scale, and proactivity allows security postures to be effective throughout all layers of an organization.
We hope you enjoyed this guest highlight from security expert Malcolm Harkins. Stay tuned for more articles and guest highlights on cloud security!